Blind (time-based) SQLi - Bug Bounty
This will be a short blog post and the first writing about Bug Bounties, I'm trying to get more involved into this matter and I'm hunting on my spare time and 90% of the time on Synack.
Early this month I got invited to a private bug bounty program running on HackerOne and for obvious reasons I'll not name the company here. As soon I got invited to the program I asked some friends that were into this very same program before myself if they knew some "fishy" areas in the application that they were willing to share with me, well this is what friends are for. :)
Talking to https://twitter.com/reefbr he sent me a self-register page in a critical domain (in-scope). The registration went through without any problem and a few seconds after hit the send button I got an email with the access details.
With my self-registered user working good it was very quick to found a file upload feature within the application. File Uploads functions are straightforward so I tried to upload a random file to see if any security control was in place by the application. The limitations that I found were:
- PDF files accept only
- AV running on the backend server
After poking around the upload function, I realise that the application was only validating the file type extension, such as "filename.pdf". I did several tries to bypass this validation and I got success in some, but in the end I did not reach any execution in the server-side, time to change the strategy.
Back in the past, when doing my official daily duties as a Penetration Tester I came across a web application that was including the filename into the database, as far I remember that time I got a Blind (time-based) SQL Injection in the filename parameter. So, why not test in this application?
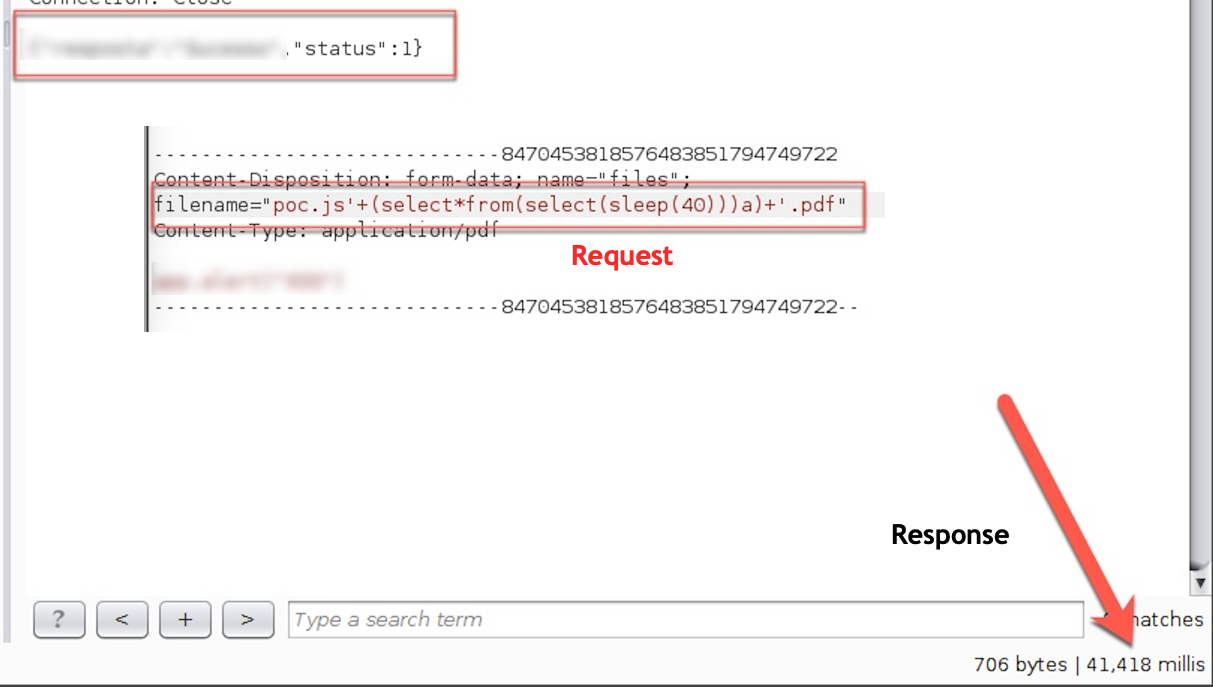
Burp Proxy set to intercept the HTTP requests, then I hit the Upload button in the application and replace the original filename parameter to:
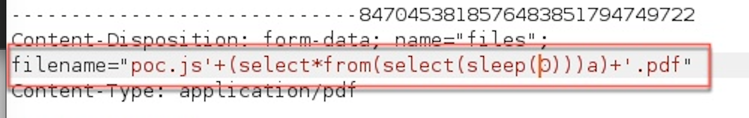
Note: I tried to send the request without the .pdf extension but the application was rejecting. BTW, this is the same payload used by the Burp Scanner for active tests.
The application was running "behind" the Cloudflare WAF, so after some tries to confirm if the application was vulnerable all my requests were getting the "Access Denied" message. Now it's time to bring back https://twitter.com/reefbr, Manoel had reported a Cloudflare bypass to the same program and again... he told me about this. Using the bypass (configuration issue) found by @reefbr I did manage to confirm the SQL Injection (finally).
Talk is cheap show me the PoC. Initial request bellow:
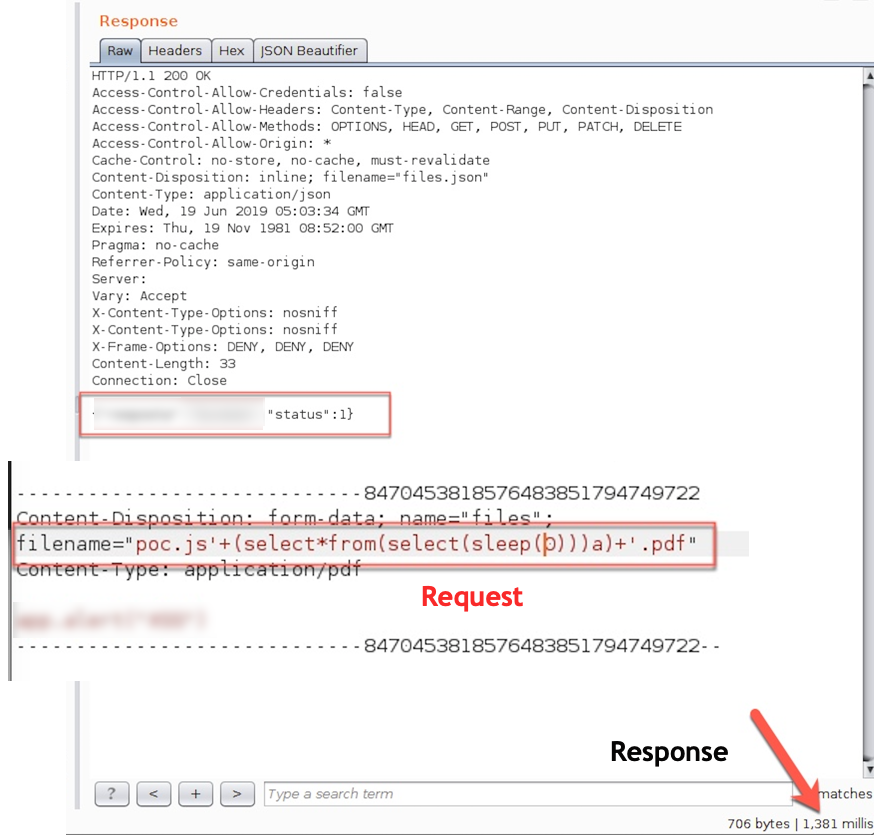
Let's increase the sleeping time...
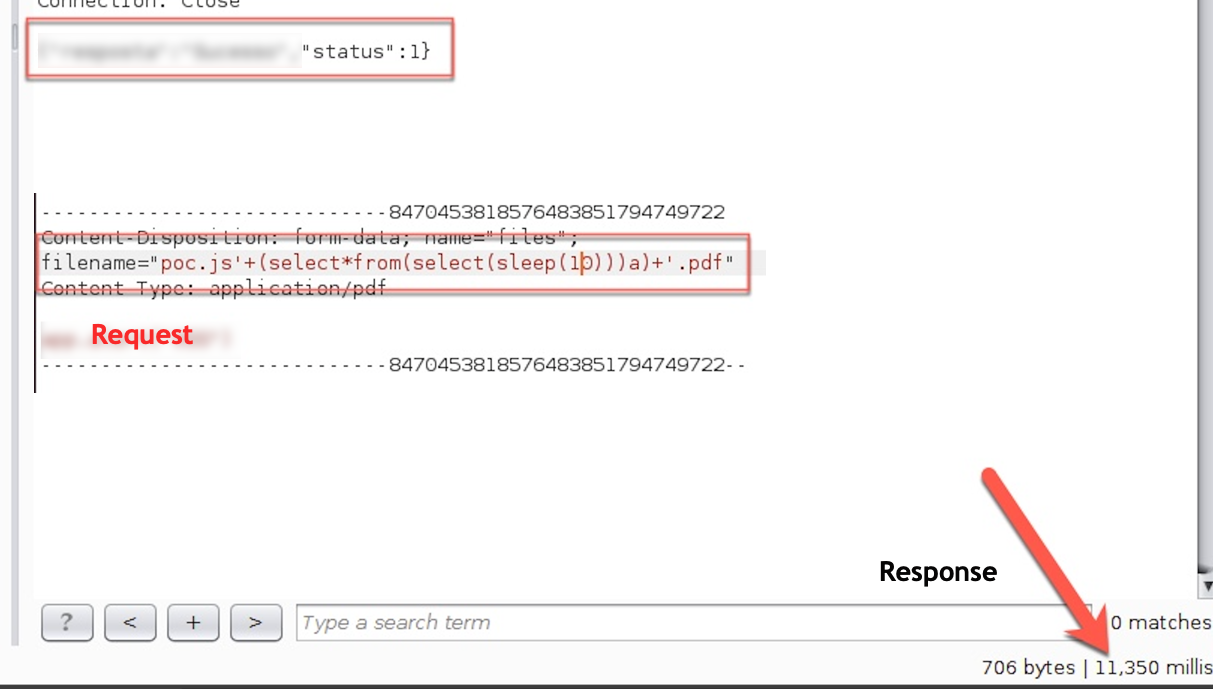
Going up a bit on the sleeping time:
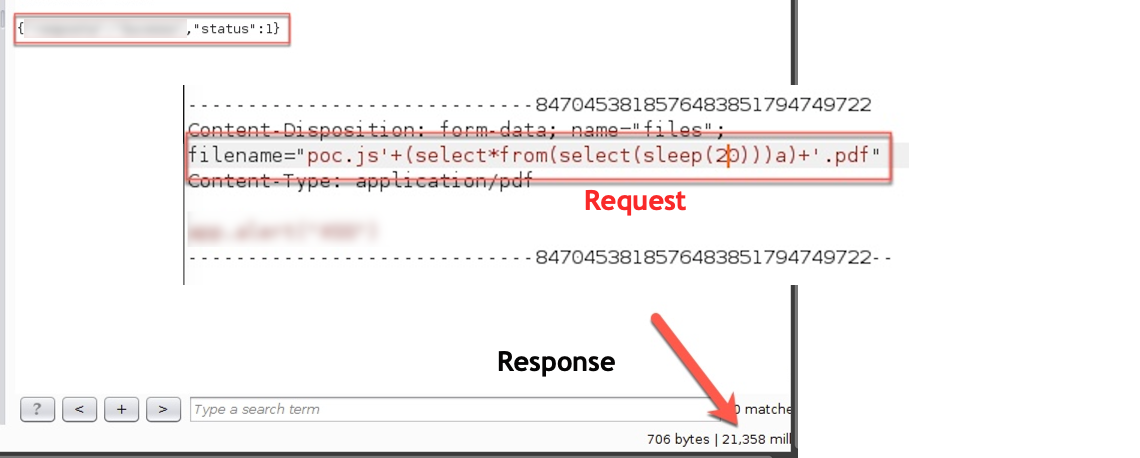
Let's make sure that the triage team will understand and be able to reproduce, so +1 request...
That's all folks, hope you did enjoy.
As a final note, this private program is handling very sensitive information (PII) so extracting any data would create new issues to the program's owner. Having this in mind, I choose to proceed with the exploitation process by using the sleep payload and comparing the responses time to proof the vulnerability.
Timeline:
- Report Sent
- Report Triaged
- Report Solved (bug fixed)
- Bounty Paid
